

Entrust established secure connections across the planet and even into outer space. We’ve enabled reliable debit and credit card purchases with our card printing and issuance technologies. Protected international travel with our border control solutions. Created secure experiences on the internet with our SSL technologies. And safeguarded networks and devices with our suite of authentication products.
The global leader in identities, payments, and digital infrastructure

Entrust keeps the world moving safely by putting secure digital transformation within reach.
Entrust keeps the world moving safely by putting secure digital transformation within reach.
Digital Security Solutions
Our identity and data security solutions help advance Zero Trust security journeys, prepare for a Post-Quantum future, and manage multi-cloud operations.
- Zero Trust – Protect identities and data, reduce risk, and achieve compliance across multi-cloud infrastructures.
- Post-Quantum Readiness – The time to prepare for post-quantum cryptography is now. PQC aims to develop new cryptographic systems that can protect against an eventual quantum attack.
- Multi-Cloud Operations – Helping organizations secure their multi-cloud and hybrid environments.
ZERO TRUST SOLUTIONS
What Is Zero Trust?
A Zero Trust framework, based on the principle of “Never Trust, Always Verify,” provides a blueprint to protecting identities and securing data in today’s multi-cloud-enabled enterprise, proactively defending against an increasingly complex threat landscape. But the path to get there remains fragmented and challenging.
Explore Zero Trust Framework Solutions

Phishing-Resistant Identities
Enable high assurance identities with phishing-resistant multi-factor authentication (MFA), including certificate-based passwordless authentication, to protect against remote-based account takeover (ATO) attacks.

Secure Connections
Establish end-to-end encryption for secure access and communications across devices, network, and cloud, with digital certificates and a comprehensive certificate lifecycle management.

Secure Data
With innovative centralized compliance management and decentralized keys and secrets storage, ensure confidentiality, integrity, and secure access to critical data while facilitating compliance with security regulations.
POST-QUANTUM CRYPTOGRAPHY
The time to prepare for post-quantum cryptography is now.
Within the decade, a quantum computer will be realized that has the computing power and stability to break the public key encryption protocols, such as RSA and Elliptic Curve Cryptography, that protect sensitive data, applications, and transactions we use every day.
There’s also the “harvest now, decrypt later” threat where bad actors are collecting sensitive data today, to decrypt once a quantum computer is capable. Don’t underestimate the effort needed to migrate to post-quantum cryptography – the effort will take years.
What’s at Risk?
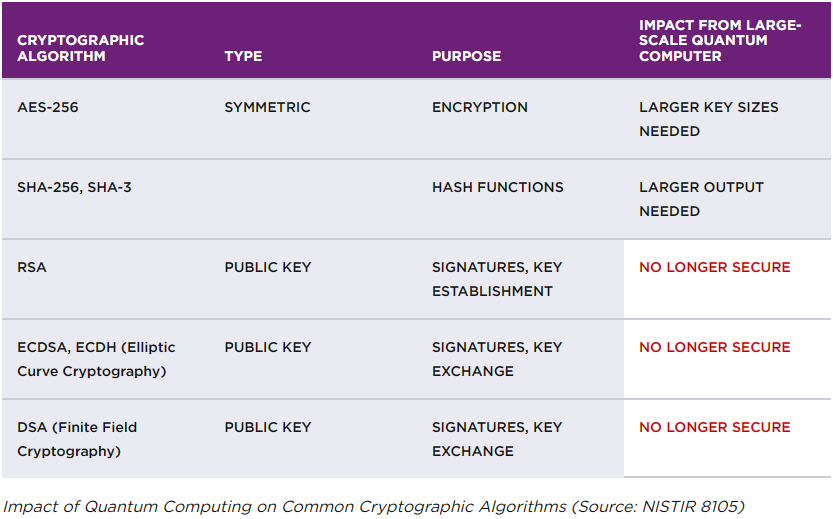
MULTI-CLOUD SECURITY SOLUTIONS
Multi-cloud security solutions that work where and when you need them
Entrust helps organizations secure their multi-cloud and hybrid environments with an enterprise-grade platform, combining cryptographic key management of VMs, containers, and secrets with compliance management. Customers benefit from a robust multi-cloud security posture that provides enterprise wide visibility, establishing robust processes while helping to prevent misconfigurations and malicious attacks.
Entrust solutions deliver a superior user experience that provides an easy way to manage workload security and faster time to value.

Key Benefits

Seamless User Experience – On-Premises, Hybrid, And Multi-Cloud Environments
Simplify authentication, authorization, and risk policy decisions.

Total Control
Our multi-cloud security solutions provide cryptographic key, certificate, secrets management, policy and compliance management, so you don’t have to give up control when you migrate to multiple cloud platforms.

Discovery, Assessment, And Monitoring
Discover and identify VM and containerized workloads, monitor, and assess compliance and risks, while providing granular automated alert and remediation capability.

Identity Orchestration Without Vendor Lock-In
Our multi-cloud security solution can bridge gaps between different identity systems to seamlessly enable, monitor, manage, and secure identity services from diverse vendors.

Lifecycle Protection
Our extensive digital signing and key management capabilities ensure data and applications are protected throughout their lifecycle.

Strong Root Of Trust
FIPS certified Hardware Security Module (HSM) root of trust for codesigning of container images for validating authenticity and integrity.
For more information – visit www.entrust.com